
Security Assertion Markup Language (SAML), which is more commonly known as Single Sign-On (SSO), is an open standard authentication service that securely lets a user connect to multiple applications with a single set of login credentials. In this GeoMarvel Live demonstration, we learn how to configure SAML with ArcGIS Enterprise with a Single Sign-On active directory account. Principles learned in this demonstration can be applied to any SAML configuration with ArcGIS Enterprise, or any other active directory service. Check out Esri’s official documentation for a full breakdown on how to Configure a SAML-compliant identity provider with a portal.
It should be noted that all ArcGIS Online and ArcGIS Enterprises connect with all SAML providers, so no matter what kind of service you’re using, as long as they have SAML integration you can integrate that with ArcGIS. ArcGIS Enterprise supports all SAML identity providers, discovering some of the common SAML identity providers that are used.
To begin this process of SAML integration for ArcGIS Online & Enterprise, users will first want to log into their ArcGIS accounts. Once logged in, navigate to the Setting tab and scroll down to the Security section. Within the Security page, you will notice a section called Login. Here you are presented with two options to choose from: New SAML login or New Open ID Connect login. We will be creating a brand New SAML login, but check out the official documentation if you’re interested in learning how to Configure OpenID Connect logins.
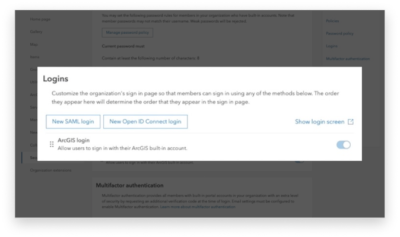
Upon clicking New SAML login, users are then presented with two options to choose from: One identity provider or A federation of identity providers. Since we are using a base active directory we will choose One identity provider. From there you will be prompted to fill out information about your organization, so users will be able to sign in to ArcGIS using the same username and password that is used with preexisting on-premise systems.
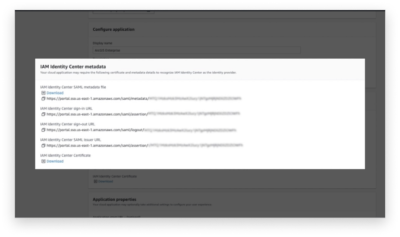
One of the major properties that are required for SAML login setup involves capturing the metadata source of Enterprise Identity Providers. In our case, we will be grabbing that information from AWS SSO. Within Amazons IAM Identity Center, users will want to select and create the application type that they desire. You can choose from a list of pre-integrated applications or in our case, a custom SAML 2.0 application. Clicking next allows you to begin configuring your application.
Within the configuration page, users are presented with a list of SAML metadata files that can easily be downloaded to XML form. Once downloaded, jump back to the ArcGIS page and drop the metadata files or links, into the appropriate spot. From there, ArcGIS will ask you to download service provider metadata which will then need to be added back on Amazon’s application page. From the application page, upload the SAML metadata file and submit it.
One thing to keep in mind with SAML integration is getting your mappings right. So once your ArcGIS Enterprise Application has been created, the next thing we want to do is start editing attribute mappings. Attributes you map become part of the SAML assertion that is sent to the application. You can choose which user attributes in the application map corresponding user attributes in the connected directory. Check out some AWS’s official documentation for some attribute mapping short-hands.
Once all attributes have been established, the next thing you want to do is assign some users to the application. From the ArcGIS Enterprise page, click assign users and scroll down to the search text bar. From here, begin to type in some usernames that you want to be added, and click assign users once finished. These users will now have access to the application.
Now that access has been granted and users are able to sign in using SSO, you can then see the new user flag, as well as all of the attribute mappings that were assigned. One final note, it should be mentioned that you can only have one SAML provider per organization. And this works identically in ArcGIS Online, there is no difference in the workflow.
This has been a brief overview on how to configure SAML with ArcGIS Enterprise with a Single Sign-On active directory account. We hope you found this demonstration to be helpful and informative during your integration process. If you like what you saw, make sure to subscribe to our GeoMarvel YouTube channel to stay up to date on all future ArcGIS-related demonstrations.
Is your organization ready for an ArcGIS Enterprise Jumpstart to get your GIS capabilities up and running? Or perhaps you’re seeking other Professional GIS Services? Explore all of our professional services, and read up on our past successes outlined in our diverse portfolio. Reach out to our industry experts to start a conversation about your unique needs today.